Explore
(Discover new Artists, Scientists, Innovators, and Trendsetters, as you explore Zedtopia...)
Harvard Gazette
Harvard professor says surveillance capitalism is undermining democracy

In her new book, “The Age of Surveillance Capitalism,” HBS Professor emerita Shoshana Zuboff outlines her belief that surveillance capitalism is undermining personal autonomy and eroding democracy — and the ways she says society can fight back.
HTTPS://NEWS.HARVARD.EDU/GAZETTE/STORY/2019/03/HARVARD-PROFESSOR-SAYS-SURVEILLANCE-CAPITALISM-IS-UNDERMINING-DEMOCRACY/Tags: surveillance capitalism, democracy
Comment
Nature
Semantic reconstruction of continuous language from non-invasive brain recordings - Nature Neuroscience
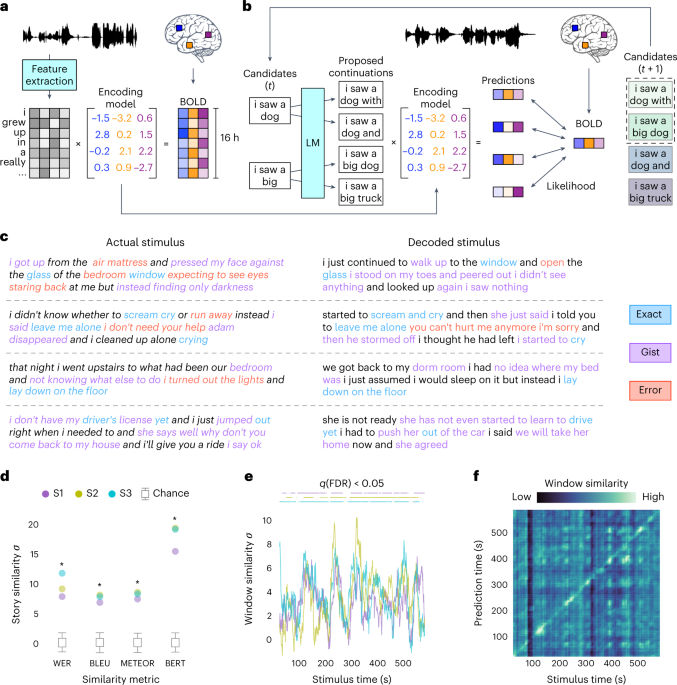
Tang et al. show that continuous language can be decoded from functional MRI recordings to recover the meaning of perceived and imagined speech stimuli and silent videos and that this language decoding requires subject cooperation.
HTTPS://WWW.NATURE.COM/ARTICLES/S41593-023-01304-9Comments
We need a Technological Constitution + Bill of Rights.
and have for decades by now….
Upvote ↑ 2 / 0 Downvote ↓Comment
HTTPS://THEINTERCEPT.COM/2023/03/21/FBI-COLORADO-SPRINGS-SURVEILLANCE/
☆ | Be the first person to star this idea.
Tags: COINTELPRO, harry belafonte
Comment
Tags: socioeconomic justice, equality
Comment
the Guardian
Sorrow and regret are not enough. Britain must finally pay reparations for slavery
In Jamaica last week, Prince William trotted out the same tired platitudes the UK has parroted for years. Now it’s time to pay
HTTPS://WWW.THEGUARDIAN.COM/GLOBAL-DEVELOPMENT/2022/MAR/29/SORROW-AND-REGRET-ARE-NOT-ENOUGH-BRITAIN-MUST-FINALLY-PAY-REPARATIONS-FOR-SLAVERY☆ | Be the first person to star this idea.
Tags: reparations, justice, No Justice No Peace
Comment
Smithsonian Magazine
Early Briton Had Dark Skin and Light Eyes, DNA Analysis Shows

The study of 'Cheddar Man' adds to a growing body of research that highlights the complexities of human skin color evolution
HTTPS://WWW.SMITHSONIANMAG.COM/SMART-NEWS/ANCIENT-BRITON-HAD-DARK-SKIN-AND-LIGHT-EYES-DNA-ANALYSIS-SHOWS-180968097/☆ | Be the first person to star this idea.
Tags: colorism, colourism, cheddar man, race is a scientifically invalid concept, we are all one people, if you go back far enough everyone is black, why we hating on our own ancestors?



lmao i used to make people jamba juice. but it's the same ish. like brooo u gotta pay somebody to make you a smoothie?!
and i'm over here like...

Upvote ↑ 0 / 0 Downvote ↓